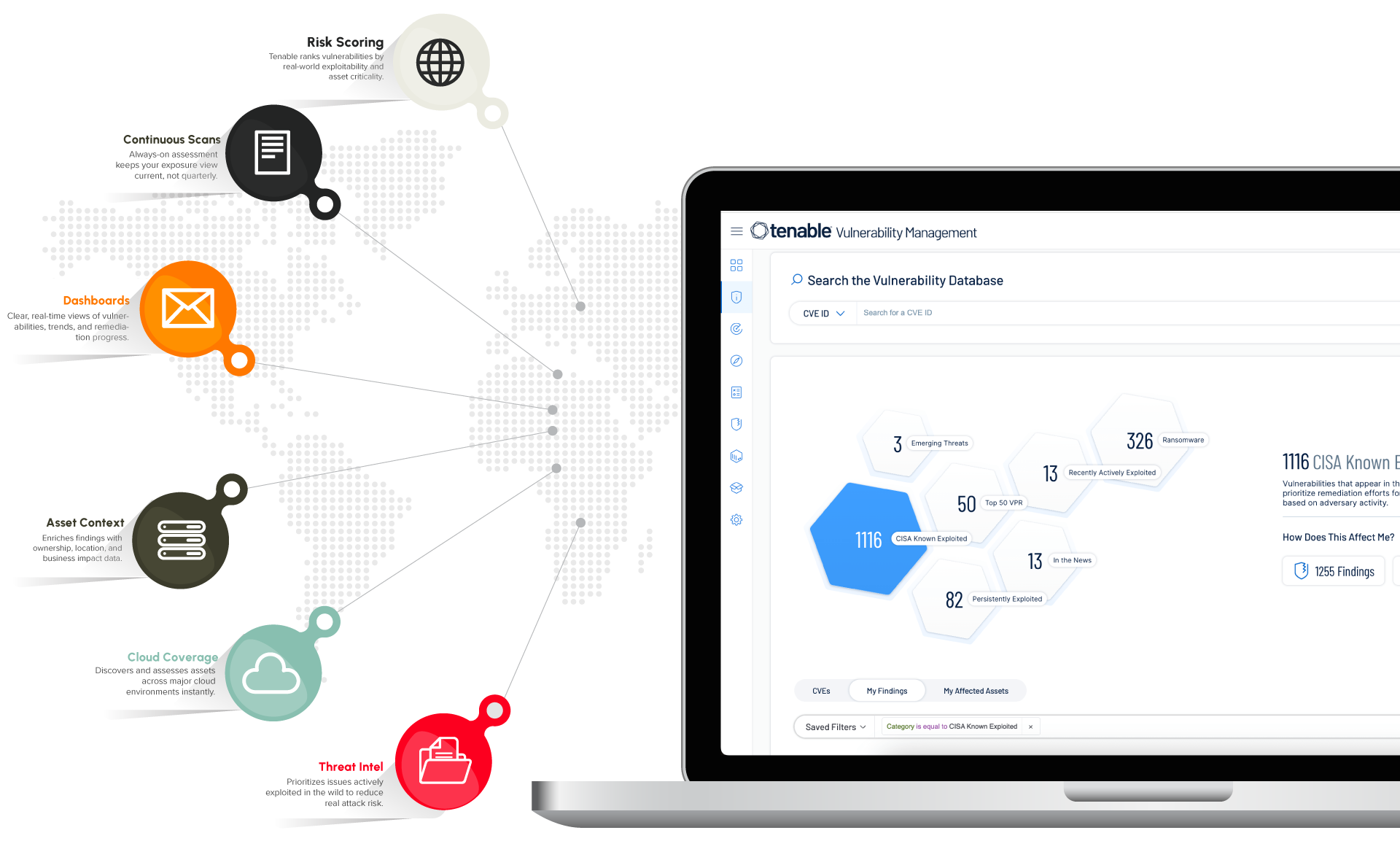
What is Managed Vulnerability Remediation?
Managed Vulnerability Remediation is a fully managed service that turns vulnerability scanning into an actionable, closed-loop process. Instead of just generating long lists of issues, we help you prioritize, assign, and drive remediation to completion.
With DataComm Managed Vulnerability Remediation powered by Tenable Vulnerability Management, we:
- Use the Tenable Vulnerability Management platform to continuously assess your assets for vulnerabilities and misconfigurations
- Prioritize findings using risk-based scoring and business context (exploitability, asset criticality, exposure)
- Coordinate with your IT and application teams to plan and track remediation
- Provide clear reporting on what’s fixed, what’s outstanding, and where risk is trending
You get an ongoing vulnerability reduction program, not just periodic scan reports.
Why do organizations choose Managed Vulnerability Remediation?
Many organizations already run vulnerability scans—but still feel exposed:.
- Scan reports are huge, hard to interpret, and quickly become outdated
- IT teams are overwhelmed and unsure where to start or what matters most
- Critical vulnerabilities remain open for months, sometimes years
- Compliance requires proof of remediation, not just proof of scanning
DataComm Managed Vulnerability Remediation closes this gap by combining Tenable’s visibility and risk scoring with DataComm’s process, people, and follow-through.
How DataComm Managed Vulnerability Remediation by Tenable works
We build a repeatable cycle: discover → prioritize → remediate → verify → report.
Discover & Assess
We begin by setting up Tenable Vulnerability Management in your environment:
- Onboard assets: servers, workstations, network devices, cloud resources, and key applications
- Configure scanners, connectors, or agents as appropriate
- Establish scan schedules and discovery methods (authenticated scans where possible)
- Build an asset inventory tied to business context (owner, location, criticality)
The result is a living view of your environment and its vulnerabilities.
Prioritize & Plan
Not all vulnerabilities are created equal. We use Tenable’s risk-based insights plus your business priorities to focus effort where it counts:
- Prioritize by factors such as exploit availability, exposure, and asset criticality
- Group findings into practical, actionable remediation bundles (e.g., by system, team, or change window)
- Define remediation targets (SLAs) based on severity and risk
- Agree on ownership between security, infrastructure, and application teams
Your teams get short, focused task lists, not overwhelming spreadsheets.
Remediate & Track
We turn priorities into action and track progress end to end:
- Create and route tickets to the appropriate IT or application teams
- Provide clear remediation guidance (patch versions, config changes, compensating controls)
- Coordinate remediation windows to reduce disruption
- Track status and follow up on overdue or blocked items
You gain a structured remediation process with visibility into what’s done and what’s still open.
Verify, Report & Improve
Fixing isn’t enough—we verify and refine:
- Re-scan to confirm that vulnerabilities are truly resolved
- Identify recurring issues or systemic gaps (missing patches, weak standards, unsupported systems)
- Provide ongoing metrics and trend reports (risk reduction, SLA performance, top recurring issues)
- Adjust priorities, standards, and processes based on lessons learned
Over time, your environment becomes cleaner, more consistent, and easier to secure.
SecurNOC is the Vulnerability Remediation solution from DataComm, built to simplify firewall administration, reduce risk from misconfigurations, and ensure your infrastructure is protected by expert oversight.
Key capabilities of DataComm Managed Vulnerability Remediation
We’ve designed our service around four core pillars.
Continuous visibility across your environment
Using Tenable Vulnerability Management, we help you maintain a near-real-time picture of your attack surface:
- -Servers, endpoints, and network devices
- Cloud infrastructure and internet-facing assets
- Key applications and services in scope
- Asset inventory integrated with business context
This lets you see where your real exposure is today—not six months ago.
Risk-based prioritization, not just CVSS lists
We focus on risk, not volume:
- Prioritization based on exploit availability, threat intelligence, and asset value
- Emphasis on vulnerabilities actively used in the wild
- Grouping of related issues into remediation campaigns
- Alignment of remediation SLAs with risk level and business impact
This helps your teams fix the most dangerous problems first.
Guided remediation workflows
We don’t just hand you a report—we help drive closure:
- Clear remediation guidance in language your IT and app teams can use
- Ticketing workflows that integrate with your existing tools where possible
- Support for risk acceptance processes and documented exceptions
- Coordination around change windows and maintenance schedules
Your teams know what to do, when, and why it matters.
Governance, reporting & compliance support
We help you show progress and meet external expectations:
- Regular reports for technical teams, management, and auditors
- Metrics on remediation time, backlog, and risk reduction over time
- Support for policy and standard development (patching SLAs, baseline configs)
- Evidence that you’re not just scanning—but actually remediating
This supports regulatory, customer, and cyber insurance requirements.
What you get with DataComm Managed Vulnerability Remediation
A typical engagement includes:
Who is DataComm Managed Vulnerability Remediation for?
This service is a strong fit if:
- You already scan with Tenable or another tool but struggle to act on the results
- Your vulnerability backlog is large and it’s unclear where to start
- Different teams own different systems and remediation efforts are inconsistent
- Compliance frameworks or customers require proof of ongoing remediation, not just scanning
- Your security team is small and needs help turning scan data into a sustained remediation program
USE CASES
Explore the Possible Applications of Vulnerability Remediation by Tenable
Closing a Long-Standing Vulnerability Backlog
You have thousands of open vulnerabilities spanning years:
- DataComm uses Tenable to re-baseline and risk-rank the backlog
- We group and prioritize issues, focusing first on actively exploited vulnerabilities on critical systems
- Over time, the backlog shrinks and a sustainable “keep it clean” process is put in place
Preparing for Compliance or Customer Audits
You need to demonstrate that you’re managing vulnerabilities:
- We align Tenable scans and reports to the relevant standard(s)
- Define and track remediation SLAs that match policy requirements
- Provide regular reports that show findings, fixes, and trends
Securing a Hybrid or Rapidly Changing Environment
New cloud resources and systems are being added constantly:
- Tenable helps discover and assess new assets as they appear
- DataComm folds them into existing remediation workflows and SLAs
- You maintain a consistent vulnerability management process across on-prem and cloud
FREQUENTLY ASKED QUESTIONS
Common questions
No. Scanning is just the starting point. Our focus is on remediation—prioritizing findings, coordinating fixes, and verifying that vulnerabilities are actually closed.
Not necessarily. If you already use Tenable, we’ll build on your existing deployment. If not, we can help design and implement Tenable Vulnerability Management as part of onboarding.
That depends on your operating model. In many environments, DataComm provides guidance and coordinates remediation while your IT teams handle patching. In others, we may be authorized to execute certain changes under defined procedures. We’ll clarify this during onboarding.
Yes. Tenable Vulnerability Management supports both traditional infrastructure and many cloud environments. During assessment, we’ll determine the best way to cover your specific mix of assets.
That depends on your risk profile and change cadence. Many organizations perform continuous or frequent assessment with regular remediation cycles (e.g., weekly or monthly). We’ll design a schedule that balances risk reduction with operational realities.
Next steps
To tailor DataComm Managed Vulnerability Remediation powered by Tenable Vulnerability Management to your organization, we recommend documenting:
- Your current vulnerability scanning tools and processes
- Asset types in scope (servers, endpoints, network, cloud, applications)
- Any regulatory or customer requirements around patching and remediation timelines
Ready to harden your network against active threats?
Schedule a Vulnerability Remediation strategy session with DataComm to review your current findings, design Tenable-based visibility, and build a remediation program that actually reduces risk.